The Internet reaches almost everywhere and contains massive source of information. How much information is accessible to the public? From the perspective of accessibility, the Internet can be divided into three layers, namely, Surface Web, Deep Web and Dark Web.
Dark Web
The Internet reaches almost everywhere and contains massive source of information. How much information is accessible to the public? From the perspective of accessibility, the Internet can be divided into three layers, namely, Surface Web, Deep Web and Dark Web.
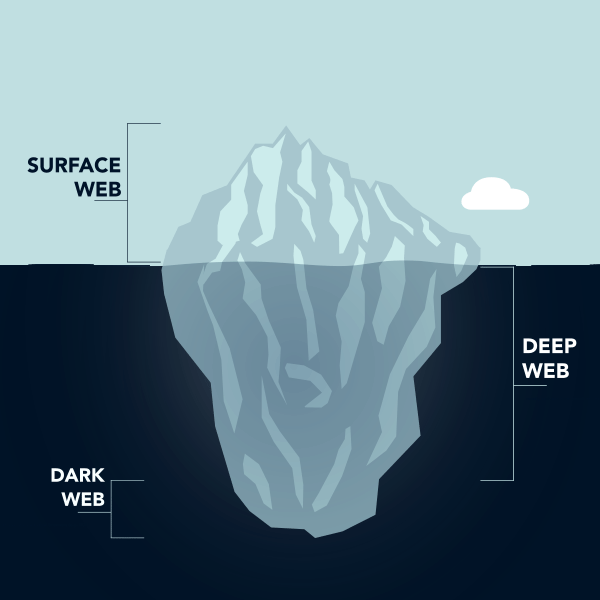
I. Surface Web
Surface Web is the portion of website and platform that facing the general public, such as news media, online shop, social platform. Their web links are searchable with standard web search engines (e.g. Google, Yahoo). The Surface Web only consists of 4% of the information that is on the Internet.
II. Deep Web
The contents on Deep web, like the company Intranet, dialogues of instant messengers, are not searchable by standard search engines. Deep Web accounts for about 90% of the information that is on the Internet. Information on Deep Web usually requires a password or other authentication to access, e.g. medical report, internal government document, commercial information, and pay-walled services such as online magazine and newspaper.
III. Dark Web (or Dark Net / Darknet)
Dark Web can only be accessible by specific software, authorisation or configurations. Most of the Dark Web users use the Onion Router (Tor), follow by Invisible Internet Project (I2P) and Freenet. The design of Dark Web allows the identities of users stay anonymous, even among Dark Web users. Information in Dark Web makes up about 6% of the Internet. The privacy and anonymity of the Dark Web are being exploited by criminals for selling drugs, weapons, child pornography, credit card, personal information, etc.
Exploring Dark Web
Tor
In the mid-1990s, staff of the United States Naval Research Laboratory considered the lack of security in online communication might cause loopholes for hackers and jeopardize the military security, so they developed Tor. The core principle of Tor is encrypting the messages in several layers. Each node in Tor adds a layer of encryption, nested like the layers of an onion. Tor websites use the domain “.onion”, unlike the common one like “.com”, “.hk”, “.org”. Visitors need to use dedicated software to access Tor sites through specific nodes.
Dark Web Abuse

Tor’s intended use is to protect the privacy of netizens, as well as their freedom of speech by keeping away from the government monitoring. However, privacy of the Dark Web is exploited by criminals for illegal activities, such as to buy and sell drugs, weapons, counterfeit currency, forged identity documents, personal information, child pornography, and even contract killing. Virtual asset transactions are often involved, which make it more difficult to investigate.
Among Dark Web market platforms, Silk Road is considered to be the most notorious marketplace that offer buying and selling of drugs. It was active in early 2011 and visited by over 100,000 users. Following continuous enforcement operations by FBI since 2013, the platform founder was being arrested and sentenced of life imprisonment for distributing narcotics, money laundering and other offences. The website has been shut down.
The world’s then-largest illegal marketplace with over 500,000 users on the Dark Net, “Dark Market”, was cracked down by Europol and international police forces in January 2021. At the time, the marketplace’s operator was arrested and the site’s servers were seized. Another enforcement operation, “DarkHunTOR”, was carried out in October 2021, in which 150 alleged Dark Net drug traffickers or criminals were arrested, together with over 31 million USD worth cash and virtual assets were frozen. Large amount of drugs and weapons were seized.
Risk of using Dark Web
The activities occur in Dark web is not beyond the law. Most of the ordinances in the real world also apply in the cyber world, including the Dark Web. Users conduct illegal transactions or activities on Dark Web may contravene relevant offences.

The number of scams and phishing traps on the Dark Web is overwhelming. Cybercriminals may set up fraudulent websites for a provision of illicit products and services at extremely low cost, then request to settle the payment in crypto assets and fled away upon receipt of payment. Besides, malware is fully alive all across the Dark Web. When the users download pirated or cracked software embedded with malicious codes, their computer devices are under high risk of being hacked or attacked by hackers, and become botnets to carry out cyber-attack against other devices.
Conclusion: Dark Web Myths
No tool guarantees absolute anonymity and safety, with no exception for Tor. If Tor are used inappropriately, the users’ personal information or IP addresses may also be compromised. In conclusion, whatever you do online are leaving footprints. Therefore, do not conduct any illegal activities.
You may be interested in
Artificial Intelligence (AI in abbreviation) is a technique of machine imitating human intelligence. In the 50’s, there were scientists suggesting…
The Hong Kong Monetary Authority (HKMA) unveiled “Fintech 2025” in the mid-2021, which aims to encourage the financial sector to…
In the digital age, teenagers have started to use the Internet since their childhood. Online content varies greatly. To what…
Some members of public might raise suspicion when receiving SMS messages from the government departments with a prefix +852 in…
Welcome to the metaverse journeyThe concept of the Metaverse originates from Snow Crash, a science fiction novel published in 1992…
NFT is a new form of virtual asset investment. Common NFT includes digital image, audio-visual file and video clip which…
The “HTTP 404” or “Not Found” page is a standard response message of HTTP status code, and it is also…
Deepfake (a portmanteau of “deep learning” and “fake”) refers to a technique using deep learning (an artificial intelligence Deepfake Deepfake…
In this era of information explosion, we are exposed to a wide variety of online media In this era of…
With the mature development of the mobile technology and cloud computing technology Digital Currency & Mobile Payment With the mature…
Cookie is a file stored in your computer or mobile, allowing the server to identify your device. What is Cookie?…
Many websites and mobile applications would collect your personal information and preference to provide more personalised experience and services, also…
In 2008, Satoshi Nakamoto published a paper on the Internet introducing a peer-to-peer electronic asset system, or Bitcoin, which used…
Misinformation refers to false information, which is deliberately created and spread to cause harm to individuals or the society. Such…
Internet of things (IoT) has been defined as a global infrastructure for the information society, enabling advanced services by interconnecting…


