Free Wi-Fi is provided in public places such as government public facilities, shopping malls
Free Public Wi-Fi
Free Wi-Fi is provided in public places such as government public facilities, shopping malls, hotels or restaurants for the public and customers to access the Internet. However, there are hidden cyber security risks when using public Wi-Fi.
Security Risks
When your mobile device is connected to a fake Wi-Fi hotspot created by hackers or one that is intruded by hackers, hackers can intercept messages and steal your personal data, account information and password, etc. They may also install malware in your devices. Most routers and smart phones can set their own service set identifiers (SSID), it is difficult to distinguish official Wi-Fi hotspots with naked eyes.
Which is the official free Wi-Fi?
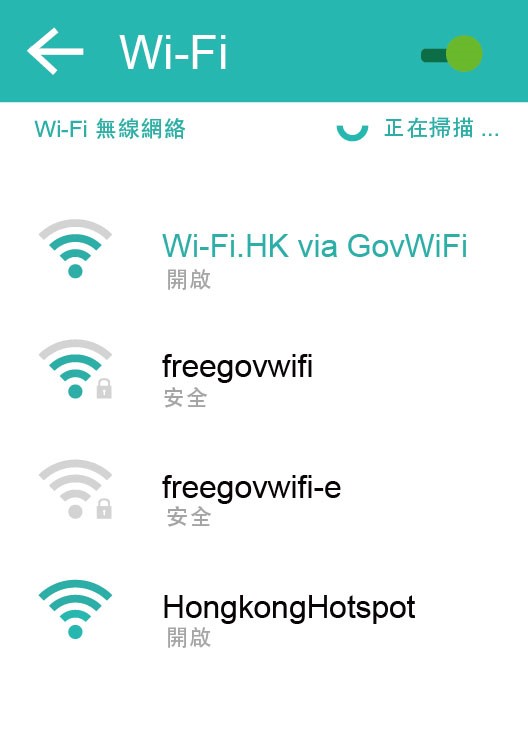
Answer: Hackers can fake any SSID (Wi-Fi hotspot name), so it is not easy to determine which Wi-Fi hotspot is really safe to use.
Tips to keep you safe on free Wi-Fi
Verify the SSID with the Wi-Fi service providers
Do not connect to unencrypted Wi-Fi hotspots
Do not transmit sensitive information or use online banking services over free network

Install firewall, anti-virus and anti-malware in mobile devices
Keep the system and applications in mobile devices up-to-date
Remove the Wi-Fi access point after use and turn off auto connect to Wi-Fi networks or hotspots
You may be interested in
A Vulnerability Disclosure Program (VDP) is a process by which an organization invites external security researchers to report vulnerabilities in…
Suspected Scam / Cyber Pitfall? Check it out with “Scameter”! Please Select Type Platform Username Platform ID Phone Email URL…
Recovery phrase is a list of words randomly generated by your crypto wallet (e.g. MetaMask) during initial account setup. Recovery…
How to set up a Firewall A firewall helps defend against cyber attacks and data breaches through shielding computer or…
A number of experts believe that spreading of virus and malware are rather difficult under iOS for the closed system…
You may have received new mobile phone as a present. After excitingly transferring data to your new mobile How to…
Cyber Security and Technology Crime Bureau, initiated a new wave of cyber hygiene operation to improve online security, maintain system…
Social media and instant messaging software have become essential tools for our daily social interaction Security of Social Media Account…
If you want to protect your computer facilities and smart devices from cyber threats, please download relevant tools via the…
Multi-Factor Authentication (MFA) is to use two or more factors to authenticate Multi-Factor Authentication and Biometric Authentication Importance of Multi-Factor…
In late 2022, a virtual private network service provider published a list of the most commonly used passwords, “password” topped…

