
Recovery phrase is a list of words randomly generated by your crypto wallet (e.g. MetaMask) during initial account setup.
Recovery Phrase
Recovery phrase is a list of words randomly generated by your crypto wallet (e.g. MetaMask) during initial account setup. Technically, it represents your private key in a human-readable format, facilitating you to write it down and remember. Once you lose your password, you will need a recovery phrase as a backup to access your wallet.
Under what circumstances will recovery phrase be compromised?
The most common case is phishing scam. There were netizens receiving phishing SMS impersonating crypto asset platform, stating that the recipient’s account will be suspended. The recipient is requested to click a hyperlink which redirects to a fraudulent website and to enter the recovery phrase. The hacker can then hijack and transfer virtual assets (e.g. Ether, USDT, NFT paintings) in the wallet using the user’s recovery phrase.
Another situation is via compromised mobile phone or computer. A hacker can hijack a user’ accounts and transfer assets using recovery phrase. Recovery phrase cannot be changed. If you suspect your recovery phrase has been compromised, you should transfer your assets to another wallet immediately.
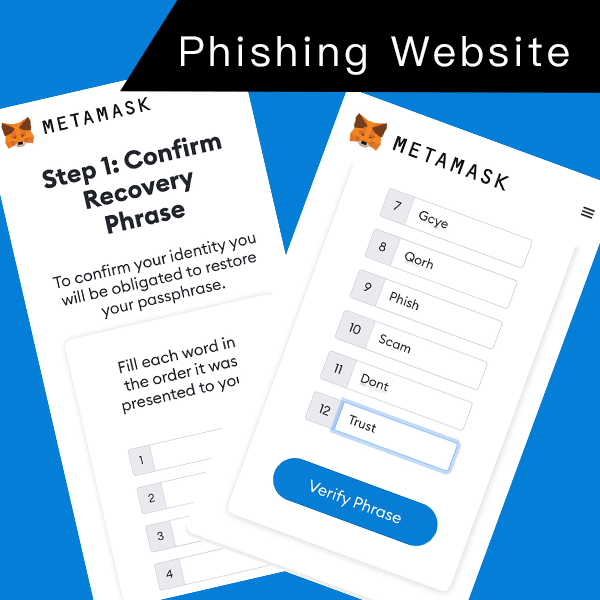
How to safeguard your crypto asset wallet?
- Write down the recovery phrase and store in a safe place like a safe deposit box.
- Enable two-factor authentication (e.g. Face ID) of your wallet to avoid being malicious hacked.
- Check authorisation on transaction platform. Delete outdated or unsure authorisation.
- Don’t open any unknown email or SMS, or click the embedded link or attachment.
- Don’t share your recovery phrase with anyone. Platform will not ask user to provide recovery phrase.
- Don’t share wallet with others.
- If in doubt, you should consult the platform.
You may be interested in
NFT is a new form of virtual asset investment. Common NFT includes digital image, audio-visual file and video clip which…
Suspected Scam / Cyber Pitfall?   Check it out with “Scameter”! Please Select Type Platform Username Platform ID Phone Email URL…
How to set up a Firewall A firewall helps defend against cyber attacks and data breaches through shielding computer or…
A number of experts believe that spreading of virus and malware are rather difficult under iOS for the closed system…
You may have received new mobile phone as a present. After excitingly transferring data to your new mobile How to…
Cyber Security and Technology Crime Bureau, initiated a new wave of cyber hygiene operation to improve online security, maintain system…
Free Wi-Fi is provided in public places such as government public facilities, shopping malls Free Public Wi-Fi Free Wi-Fi is…
Social media and instant messaging software have become essential tools for our daily social interaction Security of Social Media Account…
If you want to protect your computer facilities and smart devices from cyber threats, please download relevant tools via the…
Multi-Factor Authentication (MFA) is to use two or more factors to authenticate Multi-Factor Authentication and Biometric Authentication Importance of Multi-Factor…
In late 2022, a virtual private network service provider published a list of the most commonly used passwords, “password” topped…


