
Ransomware is a malware that prevents or restricts users from accessing computer systems. Hackers will
What is Ransomware?
Ransomware is a malware that prevents or restricts users from accessing computer systems. Hackers will infect and intrude into target computer systems via emails, websites or malicious advertisements. With ransomware installed on computers or other devices within the network, certain files such as document files, spreadsheets, digital photos, etc. will be encrypted and become inaccessible to the users. A message will then appear on victims’ computers, demanding ransom payments in Bitcoin in exchange for the decryption key.
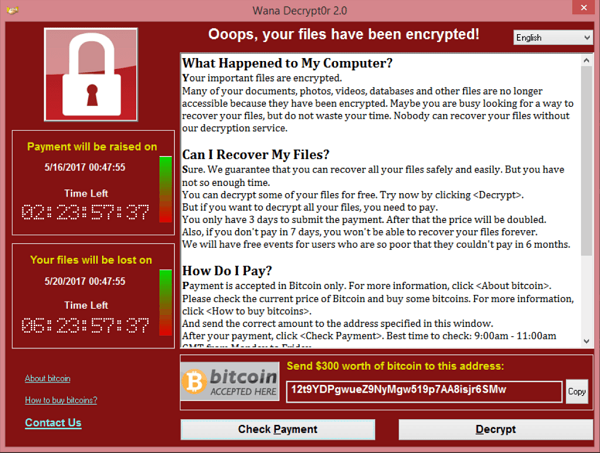
WannaCry, a ransomware, was distributed on the Internet worldwide in 2017. The infected computers displayed a ransom note with red background to notify the victims to pay in Bitcoins for decryption.

Ransomware tactics evolve over time. In recent years, hackers have started to use new tactics, namely, double extortion, triple extortion, or even quadruple extortion to attack.
Double extortion
After infecting the target computer system with tactics like phishing attack or system loophole, and making it inaccessible to the victim, the hacker would extract sensitive information of the victim. If the victim refuses to pay the ransom, he/she may not be able to decrypt the files, and the stolen files may also be made public on the Internet.
Triple extortion
Hackers extract sensitive information of the target company, including the commercial confidential information between customers or business partners. Apart from extorting money from the target companies, the hacker would also extort its customers and business partners for more ransom.
Quadruple extortion
Not limited to the above triple extortion, hackers would further threaten to launch DDoS attacks against the target companies, that is to paralyse targeted network services by flooding them with a huge volume of network traffic to force them to pay a ransom.
In early 2021, an overseas computer manufacturer was attacked by a hacker using triple extortion, involving a ransom of nearly 400 million Hong Kong dollars. The hacker stole the product design plans between the company and its partner, and warned them if ransom was not paid in time, the amount would be doubled. As the company refused to do so, the hacker published its design plans online successively, and even extorted payment directly from its partner.

Security Tips:
- Perform regular backups on important data and keep the backup copies disconnected from the computer
- Install the latest patches for operating systems and software in use
- Keep your anti-malware program and signatures up-to-date
- Schedule a regular full scan to detect and guard against malware attacks
- Do not open any suspicious emails or instant messages, as well as the attachments and hyperlinks inside
- Refrain from visiting suspicious websites or downloading any files from them
What should I do if infected?
- Disconnect the network cable of the computer to avoid affecting network drives and other computers
- Power off the computer to stop the ransomware from encrypting more files
- Jot down the programmes and files executed, emails opened and websites accessed before the infection, and report to the Police
- Recover the data from backup to a clean computing device
- Do not pay the ransom. Paying a ransom does not guarantee that you will get the decryption key, but emboldens hackers to commit crimes.
Reference:
- 香港警務處-電腦勒索軟件攻擊
- 網絡安全資訊站-預防勒索軟件
- 香港電腦保安事故協調中心 - 勒索軟件的進化:雙重勒索和虛假解密工具
- 香港電腦保安事故協調中心 - 勒索軟件不斷進化:多重勒索
- paloalto - Ransomware Crisis
- I Know科技產業資訊室 - 三重勒索、攻擊供應鏈及遠端網路攻擊持續增加
- Check Point - Check Point Software’s Mid-Year Security Report
- 資安趨勢部落格 - 2022 年資安預測重點:駭客藉「四重勒索」擴大獲利、供應鏈成駭客攻擊新場域、個資外洩風險攀升
- Trend Micro - Trend Micro Security Predictions for 2022
You may be interested in
Fraudsters steal information through the Internet such as names Identity Theft Fraudsters steal information through the Internet such as names,…
refers to an attack in which. attacker monitors the communication between the sender and What is Man-in-the-middle Attack? A man-in-the-middle…
An APT is a common cyberattack which is meticulously planned against specific What is an APT attack? An APT is…
The Internet of Things is a system of mobile devices or household equipment What is Internet of Things (IoT)? The…
Hackers utilise multiple infected computer systems (i.e. Botnet) to generate huge volumes of traffic, overloading the What is Distributed Denial…
Phishing attack is a prevalent cybercrime which can take various forms. What is phishing attack? Phishing attack is a prevalent…


